
Wallet
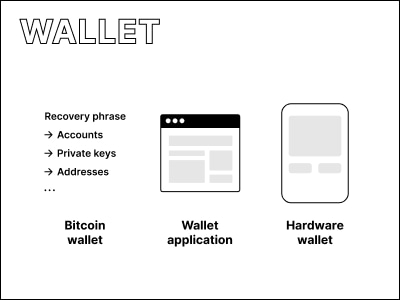
Bitcoin wallet #
All bitcoin-related data derived from and associated with a single recovery phrase. Most modern bitcoin wallets are HD wallets.
HD wallet #
Hierarchical Deterministic wallets, or HD wallets, can create infinite keypairs organized in a tree-structure (hierarchical) from a single (deterministic) controlling keypair. They were introduced and defined in BIP32 and then expanded with BIP44 which added the ability to handle multiple accounts in one wallet.
Technicalities - There are different bitcoin address formats (see address). They have to be held in different branches of the HD wallet but can be controlled by the same recovery phrase.
Hardware wallet #
A hardware device used to manage a bitcoin wallet. More on the Hardware overview page.
Wallet application #
A software application used to manage a bitcoin wallet. More on the Software overview page.
Non-custodial / Custodial wallet #
Also known as unhosted / self-hosted / hosted wallet.
A non-custodial wallet-application implies that the private key and/or recovery phrase is in full control of the end-user. This means that transactions can never be made without the user’s direct action. It also means that should the user forget or misplace their recovery phrase, wallet-application makers cannot help restore access to the funds in the bitcoin wallet. This guide is focused on non-custodial wallets.
With a custodial wallet-application, the users are not exposed to and in charge of securing the recovery phrase. Often custodial wallet-applications require users to sign in with their email and password. Users must trust the wallet-application makers to secure their recovery phrase and bitcoin. With a custodial wallet-application, the makers of it are technically in control of their users’ funds. Most exchanges give users custodial wallets.
Hot / Cold wallet #
Hot and cold describe a wallet in terms of being connected to the internet. Where a hot wallet is connected to the internet, a cold wallet is not. The idea is that a cold wallet is less susceptible to third-party theft over the internet. Most software wallet-application would be seen as hot (although some can be used just for signing on a device not connected to the internet), and most hardware wallet-application would be seen as cold (although they are sometimes connected for signing purposes).