
Wallet privacy
Privacy is about the ability to control what information is available to others. On this page, we will provide a soft introduction to the topic, with a focus on what product builders and users can do to improve their payment privacy.
Design with privacy in mind #
Thinking about privacy is critical during the design process. Your users will not have the same level of knowledge of how to use bitcoin privately. The privacy by design framework states that privacy should be incorporated and built into products by default. This way, whether or not the user is concerned with their data privacy, they would always be protected through good UX and UI.
However, it still is important to help users understand any actions that might impact their privacy. Most of the risks occur at the point of creating a transaction or requesting a payment, and we should try to design solutions that reduce the risk of unknowingly degrading privacy.
While there is no perfect solution that will guarantee 100% privacy, try to minimize how much information gets shared to the most essential. Consider ways to inform and prevent user actions that negatively impact their privacy as they use your product.
Real-world privacy #
Exposing wallet information to others around you can be a problem in terms of security and privacy, as well as personal comfort. Sensitive information includes:
- Wallet Balance - shows how much is owned
- Transaction history - reveals payment partners and purposes
- Addresses - can be used to track on-chain transaction history
- Invoices - can be used to track lightning payment history
- Recovery phrase - can be used to access and transfer bitcoins
It’s more common for wallets to protect private keys, but not much is done for other sensitive information like the balance, addresses, and previous transactions. A few wallets like Bitcoin Core, Wasabi, Muun, and others have made it work, though. For patterns and considerations for hiding and revealing sensitive information, see the privacy page in the daily spending wallet reference design.
Third-party services #
Whether it is for retrieving exchange rates or using lightning services, interacting with centralized third parties can leak user data. You may want to allow users to disable those features, choose the services they use, or use another method of anonymizing requests. It is also essential to only expose your users to services that you have vetted and deemed trustworthy.
Data transfer #
Option to enable Tor in settings.
Internet service providers and similar services that handle data in transit may be able to gather or infer information about the user from the traffic. Tools like VPNs and Tor can prevent this by adding additional layers of encryption and masking user activity. Keep in mind that using Tor provides better privacy but can noticeably slow down the experience (especially initial startup).
Lightning network #
On the lightning network, a payment is only stored by the respective sender and receiver, and only as long as the channel in which the payment was made is open. However, opening and closing channels requires entries on the bitcoin blockchain, and those are also publicly stored forever. Additionally, lightning nodes are always online and usually directly tied to a single wallet, providing another data point. For a detailed analysis of privacy on lightning, see the Security and privacy chapter in the Mastering the Lightning Network book.
Sharing static lightning identifiers #
Lightning node Ids, lightning addresses, and LNURL-Pay invoices (see Payment request formats) are examples of endpoints that can be used to generate many lightning invoices. While this is convenient for users, it is bad for privacy. For example, placing a lightning address on a website or social media profile makes it trivial to create a direct connection between the lightning node and the owner of the website or profile.
Bitcoin network #
By default, data is pseudonymous on the bitcoin networks.
It’s a common misconception that bitcoin payments are anonymous. Rather, bitcoin payments are pseudonymous, meaning no identifiable information is tied to transactions. Unless ownership is revealed, whether by the parties involved or some third-party, payments remain anonymous.
Transactions, their signatures, and addresses added to the bitcoin blockchain remain public forever. This means that looking up any address or transaction is trivial, as demonstrated by going back to the very first block mined on January 3, 2009. The key to keeping your transactions private is to prevent others from determining which addresses you own. Since Satoshi let others know that they had mined the first block, which contained a single transaction, one can deduce that both the address that received the block reward and the sender address in the transaction belongs to Satoshi. This illustrates the permanence of associations between addresses and identity. While it’s possible to break assumptions of ownership going forward, the challenge is to recover privacy once an association is made public. That being said, in this case, the pseudonym “Satoshi Nakamoto” has yet to be associated with any personal identity.
Each bitcoin transaction contains at least one input and at least one output. This means that once a single address is known, there is a trail to follow the bitcoin.
As documented by Wasabi Wallet
There are many ways your identity might get connected to your wallet and payments, so keeping bitcoin payments private takes diligent work but is not impossible. Let’s explore some practices that help preserve the privacy of bitcoin payments.
Generate a new address for each on-chain payment #

A new address should be generated for every payment.
A new address should be generated by the wallet application any time the user wants to receive bitcoin on-chain. This is achieved by using HD Wallets, a standard in modern bitcoin applications that can generate and manage an infinite number of addresses without revealing their common root.
This allows each incoming transaction to use a new address that is unconnected to any other in the wallet, making it difficult to associate with the owner.
Address reuse degrades the privacy of both the sending and receiving parties. Reusing an address on the receiver’s side means that anyone with whom that address is shared can see previous payments and the amount of bitcoin controlled by that address.
If bad actors can see your income, holdings, and spending, they can use this information to target and exploit you.
By sending to an address that is being reused, the sender is now traceable and connected to any previous transactions the receiver has made with that address. This increases the risk of exposure to an adversary.
Do's
- Generate a new address any time the user wants to receive bitcoin
- Make it easy to generate as many addresses as the receiver needs
- Warn the user if an address has already been used before broadcasting a transaction
Keep track of who knows about on-chain addresses #
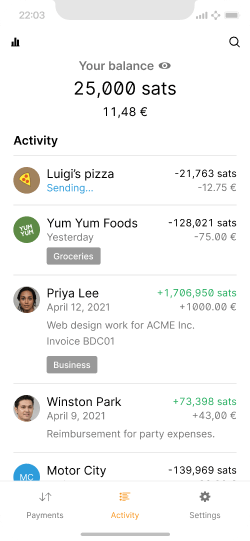
A well-annotated transaction list can simplify privacy management.
There are multiple benefits to users adding contacts and additional details to transactions. It helps remember what payments were for and also enables preventative measures for preserving privacy. In future transactions, it becomes easier to send coins (UTXOs) that do not reveal parts of the user’s transaction history that they are uncomfortable being public knowledge. This is often referred to as coin control.
As it is complex for users to manually keep track of this, most wallets automate the process and offer access via non-default settings.
Using multiple wallet applications #
Another simple way to avoid data points from being connected is for users to set up and use multiple wallets or accounts for different purposes. For example, if a user wants to set up a page to collect tips on their website, they can set up a dedicated wallet. Anyone analyzing the activity around the wallet would only see incoming tips and none of the other activity that happens in other wallets the user controls. Users just need to be careful with on-chain cross-wallet transfers, as those can allow observers to connect the wallets again.
More information #
- Protect your privacy (bitcoin.org)
- Privacy (Bitcoin Wiki)
- Lightning privacy (Concerns and Solutions) (presentation at Bitcoin Miami 2022)
- Lightning Service Providers and Liquidity (presentation at Bitcoin Miami 2022)
- State of Lightning Privacy in 2021 (A Byte’s Journey)
Next, learn how bitcoin wallets can offer authentication and payments to other applications and web services via sign in with bitcoin.